
If you're like most organizations, your ETL process is the lynchpin of your data infrastructure. So ensuring this process's security is critical to protecting your data and preventing costly outages. But keeping your ETL process secure can be tricky, especially if you're unsure where to start.
Not to worry! We've put together a helpful guide to ensure you get started.
Why security is vital for ETL processes
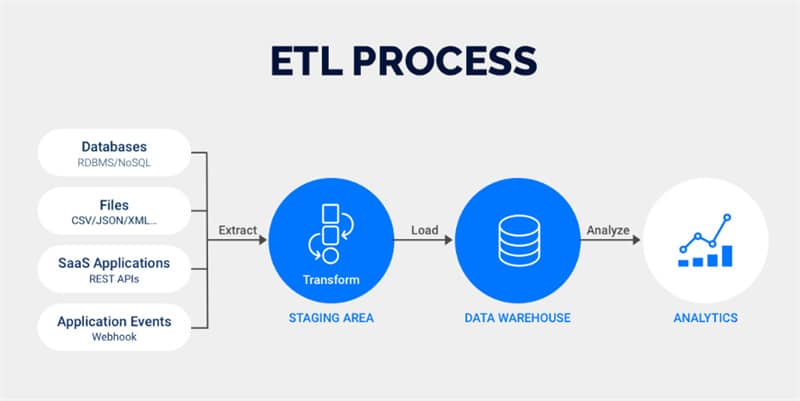
Your ETL process is responsible for extracting, transforming, and loading data from various sources. This data may include sensitive customer records, financial data, or personal health information.
If this data gets into the wrong hands, criminals can use it to commit fraud, identity theft, or other crimes. Additionally, a breach of your ETL process could result in significant financial losses for your organization.
Best practices for keeping your ETL process secure
You can take a few simple steps to help keep your ETL process safe. These include:
Consider on-premise ETL
As companies increasingly look to On Premises ETL solutions to move their data, it's essential to keep security in mind. One best practice is to use encryption to protect sensitive data, which can help ensure that only verified users have access to data and that even if it is intercepted, it would be tough to decrypt.
Various encryption algorithms are available, so choosing one that is both effective and efficient for your particular ETL process is essential. With proper encryption in place, you can help keep your ETL process secure and protect your data.
Using trusted sources for your data feeds
One of the essential aspects of ETL security is ensuring that you only use trusted sources for your data feeds, which may seem like a no-brainer. However, it's incredible how many companies fail to follow this simple rule. After all, if you can't trust your data source, how can you trust it?
There are a few ways to ensure that your data sources are trustworthy:
- Check to see if the reference has been certified by a reliable organization.
- Ensure the data is encrypted before it being sent to you.
- Look for sources that have a good reputation among other users.
Use strong passwords and change them often

Using strong passwords and regularly changing them is crucial to secure your ETL process.
One way to create strong passwords is to combine upper and lowercase letters, numbers, and special characters. Another practice to put in place is to use various passwords for different applications.
That way, if one password is compromised, the others will still be safe. And finally, it's essential to change your passwords regularly. A good rule of thumb is to alternate them every 90 days.
Keeping your software up to date
One of the most vital activities you can do to keep your ETL process secure is to keep your software up to date. Outdated, old software is one of the most common security risks and is often the target of attacks.
By making sure your software is up to date, you can help protect yourself from known vulnerabilities. In addition, always use strong passwords and never reuse passwords across different systems.
Final thoughts
ETL processes are critical to businesses of all sizes, and keeping them as secure as possible is essential. Following the mentions in this blog post, you can ensure that your data is protected from unauthorized access and theft.
In addition, remember to use strong passwords, update your software regularly, and train your employees on security best practices.










