
The cloud is changing the way organizations approach security. Instead of building their own data centers (and hiring armies of specialized engineers), companies can now buy what they need on-demand when they need it.
Security services are no exception, and there are several third-party options available.
But how do you know what you're getting? These services can help protect your data and systems from attacks, as well as keep your business running smoothly.
Here are ten Azure security services you can expect from a cloud security service provider.
1Security Assessment and Consulting
Security Assessment and Consulting

According to reports, 61 percent of healthcare businesses acknowledged they don't have effective mechanisms to maintain proper cybersecurity.
One of the best ways to secure your Azure solution is by getting an expert opinion on how to set it up.
A good cloud security service will advise you on what security safeguards are appropriate for your business and which ones can be relaxed based on your organization's risk tolerance.
2Security Architecture Consulting
Security Architecture Consulting

Once the vulnerabilities have been found, the consultant will help you develop a security architecture that addresses them.
The architecture should be deployed in a piecemeal fashion so that you can implement one new safeguard at a time. If there is a problem with the new security implementation – it will be easier to identify and fix.
It will include designing a secure network, implementing access controls, and setting up the appropriate systems.
3Security Engineering
Security Engineering

From securing an Azure virtual machine to designing a secure cloud strategy, security engineering is where third-party consultants become indispensable.
They can help you set up firewalls, intrusion detection/prevention systems (IDS/IPS), and malware scanning.
On top of that, they will also design the implementation plan for your organization's needs and provide you with documentation on the new system.
4Threat Modeling Consulting
Threat Modeling Consulting
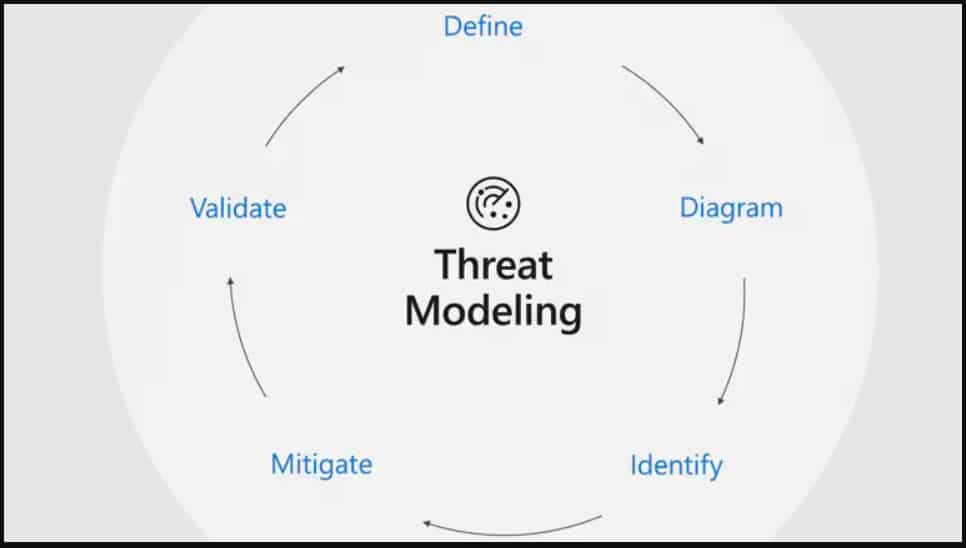
Threat modeling is the process of identifying and assessing potential threats to your system. Azure security services can help you identify which threats are most likely to affect your business and develop a plan to mitigate them.
Threat modeling includes identifying threats to your environment. Whether you use Azure or some other cloud service, third-party consultants can help you create a threat model for your business's unique needs.
5Penetration Testing
Penetration Testing
Perfect security is a myth, and an experienced consultant can help you identify vulnerabilities in your system before hackers exploit them. Penetration testing helps companies reduce the risk of a potential breach and decreases its severity when one does occur.
It also ensures that your systems work correctly and minimizes the chances of data loss.
6Risk Assessment
Risk Assessment
A risk assessment is a critical part of any security strategy, and Azure security services can help you identify and quantify your organization's risks.
It allows you to decide which security measures are necessary and which ones can be relaxed based on your risk tolerance.
7Vulnerability Scanning
Vulnerability Scanning

Vulnerability scanning is the process of identifying security holes in your system. Third-party consultants can use automated tools or manual testing to find these vulnerabilities and then help you fix them.
8Security Operations
Security Operations
A cloud security service can also help you set up and manage your security operations.
It includes the development of policies and procedures, the training of staff, and the implementation of monitoring and detection systems. Security operations teams will analyze the data, determine the threat level, and take appropriate action.
9Identity and Access Management
Identity and Access Management
Identity and access management or IAM manages who has access to which resources in your system. IAM systems can be complex, and it is essential to get expert help when implementing them.
A sound IAM system will ensure that only authorized users have access to sensitive data and that this access is strictly controlled. It will also help you manage your passwords and user profiles.
10Compliance Consulting
Compliance Consulting

Cloud security is not just about protecting your system from hackers. You also need to make sure that you follow the necessary security policies and laws.
It means meeting compliance requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) or Payment Card Industry Data Security Standard (PCI DSS).
A third-party consultant can help you develop a compliance strategy that meets all your needs.
As companies become more reliant on cloud services, they also increase their exposure to security risks. Hackers can take advantage of vulnerabilities in your systems and cause serious problems, whether a data breach or a complete system failure.
If you use Azure, the good news is that you have access to a wide range of cloud security services that work in integration with Azure.
However, it is crucial to understand that these services are only a starting point. You may also require to enlist the help of a third-party consultant if you want to make sure that your system is fully secure.










